To sign a URL for private distribution's object, you firstly need to setup a private distribution with read permission to your S3 objects. Check
this blog for how to properly setup the private distribution.
To create the sign URLs, you can select the files you want to sign, and choose "URL..." from the popup menu. The URL will be shown to assist your URL Sign tasks. Our URL generator dialog can detect whether an S3 object is associated with private Download/Stream distribution, and then assist to create the corresponding HTTP/HTTPS/RTMP/HTML URLs, as shown in Fig. 1.
Fig. 1. URL Dialog
Before start to sign the URL, defining the secure signing policy's definition is a precondition:
Secure Signing Policy
You can setup the signing policies by choosing Tools -> Policies, or in the URL dialog and press the Signing policy: Configure button.
The policies list dialog will be shown as Fig. 2. You can use "New" button to create the new policy, "Edit" button to edit an existing policy, "Delete" button to remove a policy, "Save as" and "Load from" button to export/import the policies.
Fig. 2. Policies Dialog
There are two types of signing policies: Canned Policy and Custom Policy. Here we introduce these policies one by one:
Canned Policy: a "simplified" policy definition that uses default options for your signed URL's behaviors, as shown in Fig. 3. Key pair ID and Private Key file are the most importation items in this dialog.
Fig. 3. Canned Policy Modification
- Key pair ID is the ID number you will get from Amazon when you generate a Key Pair using Amazon web interface or when you upload your own key.
- Private Key File is the file you downloaded from Amazon web interface when you generate a Key Pair, or the private key file you used to generate the Key pair for uploading to Amazon.
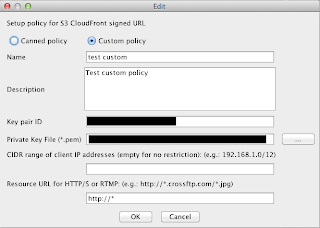
Custom Policy: a policy describes custom access permissions to apply via a private distribution's signed URL, as shown in Fig. 4. Compare this with the Canned policy, we can find that two important items are added here: CIDR range and Resource URL.
Fig. 4. Custom Policy Dialog
- CIDR range: An optional range of client IP addresses that will be allowed to access the distribution, specified as a CIDR range.
- Resource URL: An optional HTTP/S or RTMP resource path that restricts which distribution and S3 objects will be accessible in a signed URL. For standard distributions the resource URL will be "http://distributionName/objectKey" (may also include URL parameters). For distributions with the HTTPS required protocol, the resource URL must start with "https://". RTMP resources do not take the form of a URL, and instead the resource path is nothing but the stream's name. The '*' and '?' characters can be used as a wildcards to allow multi-character or single-character matches respectively.
Generate signed URL for Private Distribution
URL dialog checks the S3 objects' associated distribution, and adds the private distribution's domain name/CNAMEs in the CNAME dropdown box. The URL dialog supports to generate HTTP/HTTPS/RTMP/HTML/FTP/Path type URLs.
For the download distribution, you should choose HTTP/HTTPS radio button, choose the
prefixed distribution URL in CNAME drop-down box, select the proper signing policy, and then press "Generate" button to sign the distribution, as shown in Fig. 1.
For the stream distribution, you should choose RTMP/HTML radio button, choose the
prefixed distribution URL in CNAME drop-down box, select the proper signing policy, and then press Generate button to sign the distribution, as shown in Fig. 5.
Fig. 5. Sign URL for Stream Distribution
Conclusion
CrossFTP Pro makes it easy to manage your CloudFront distribution and URL signing.
This feature is available for CrossFTP Pro 1.86.2 or later.
--
CrossFTP is a
FTP,
SFTP,
FXP,
WebDav,
Amazon S3,
Amazon Glacier and
Google Cloud Storage client for Windows, Mac, and Linux.
CrossFTP Team
http://www.crossftp.com/