To improve Mac users' installation experience, we have now delivered CrossFTP Pro into the Mac App Store. You can find the Mac App Store link at:
https://itunes.apple.com/au/app/crossftp-pro/id574356166?mt=12
Fig. 1. is a preview of the CrossFTP Pro in the store.
If you are a happy user of CrossFTP Pro, welcome to add reviews in the App Store so that more users will know about us.
Note: Since Mac App Store enforces the security entitlement of applications, CrossFTP Pro's Mac App Store version is limited to visit the "Downloads" folder only due to the Sandbox policy. If you need to visit files outside the "Download" folder, you can download the standard CrossFTP from our download page. It will automatically recognize your Mac App Store's purchase, and run as a registered CrossFTP Pro version.
--
CrossFTP is a FTP, SFTP, FXP, WebDav, Amazon S3, Amazon Glacier and Google Cloud Storage client for Windows, Mac, and Linux.
CrossFTP Team
http://www.crossftp.com/
Friday, December 14, 2012
Thursday, November 29, 2012
CrossFTP 1.88.4 Released
CrossFTP 1.88.4 is a major update. The main changes are:
* Support S3 Sydney Bucket Location.
* Fix some file upload issues for Google Cloud Storage.
This update is recommended for all CrossFTP users.
CrossFTP is a FTP, FXP, WebDav, Amazon S3 and Google Cloud Storage client for Windows, Mac, and Linux.
CrossFTP Team
http://www.crossftp.com/
* Support S3 Sydney Bucket Location.
* Fix some file upload issues for Google Cloud Storage.
This update is recommended for all CrossFTP users.
CrossFTP is a FTP, FXP, WebDav, Amazon S3 and Google Cloud Storage client for Windows, Mac, and Linux.
CrossFTP Team
http://www.crossftp.com/
Thursday, November 22, 2012
How to use CrossFTP to connect to Google Cloud Storage
To connect to the Google Cloud Storage, please select the Google Cloud Storage in the protocol list box in the CrossFTP's site manager. There ate two different authentication approaches available for the Google Cloud Storage: Access key based and Oauth2 based. We will introduce these two approaches separately in the following:
- Access key based - you should copy the access key and the secret from the Google's online management console - Storage - Cloud Storage - Project Dashboard - Interoperable Access (instruction link), and fill on the corresponding field in the site manager, as shown in Fig. 1.
Fig. 1. Access Key for Google Cloud Storage Protocol
- Oauth2 based (HTTPS only) - you should fill in the project number and then click to connect, as shown in Fig. 2. If this is the first time you connect to the site, a dialog will be popped up with an authentication URL. You should open this URL in your web browser, and copy the authentication code back into the dialog, as shown in the Fig 3. and Fig.4.
Fig. 2. Input Project Number
Fig. 3. Authentication Dialog
Fig. 4. Agree the Access Permission, and Copy the Code Back to Authentication Dialog
Once connected, you can create new buckets, modify the file object's permission and metadata, and define the bucket logging on the Google Cloud Storage.
Conclusion
CrossFTP Pro makes it easy to manage Google Cloud Storage sites.
This feature is available for CrossFTP Pro 1.88.2 or later.
--
CrossFTP is a FTP, SFTP, FXP, WebDav, Amazon S3, Amazon Glacier and Google Cloud Storage client for Windows, Mac, and Linux.
Monday, November 19, 2012
CrossFTP 1.88.2 Released
CrossFTP 1.88.2 is a major update. The main changes are:
* Support Google Cloud Storage
* Improved metadata editing tool
* Better support of 3rd party S3 sites API
* Add wizard for Walrus
* Add wizard for DreamObjects
This update is recommended for all CrossFTP users.
--
CrossFTP is a FTP, SFTP, FXP, WebDav, Amazon S3, Amazon Glacier and Google Cloud Storage client for Windows, Mac, and Linux.
CrossFTP Team
http://www.crossftp.com/
* Support Google Cloud Storage
* Improved metadata editing tool
* Better support of 3rd party S3 sites API
* Add wizard for Walrus
* Add wizard for DreamObjects
This update is recommended for all CrossFTP users.
--
CrossFTP is a FTP, SFTP, FXP, WebDav, Amazon S3, Amazon Glacier and Google Cloud Storage client for Windows, Mac, and Linux.
CrossFTP Team
http://www.crossftp.com/
Thursday, November 15, 2012
How to Connect to Multiple Sites with CrossFTP
Open New Tab
Connect and manage multiple FTP sites simultaneously are of extreme importance for heavy FTP users. You can easily achieve this in CrossFTP to improve the working efficiency. To do this, simply choose the file pane you want to add a new connection tab, and select Tab -> New Remote Tab to open a new FTP file tab, or select Tab -> New Local Tab to open a new local file system pane. This is shown in the Fig. 1.
Fig. 1. Open New Local/Remote Tab
Site-to-Site/FXP Transfer
If you open a remote site on the left and right pane simultaneously, you can easily do the site to site (FXP) directly by transfer the files from one pane to another pane. Currently we support the traditional FXP transfer, S3 to S3's transfer, and WebDav to WebDav site's transfer in this mode.Switch between Multiple Tabs
You can switch between different sites simply by click on the corresponding tabs, similar to the modern multi-tabbed web browser. Each tab title shows the site's favorite icon, as well as the folder's name. This is shown in Fig. 2.
Fig.2. Switch between Multi-Tabs
Favorite Bookmarks
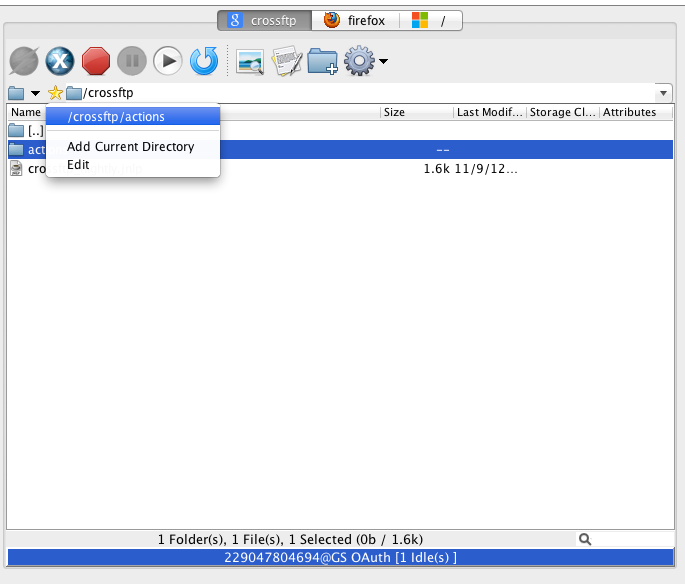
Favorite directory bookmark is another browser-like feature you would want to use when managing many different file locations. This is shown in the Fig. 3.- Add New Bookmarks: simply click on the star icon to bookmark, and choose "Add Current Directory" to add a new folder bookmark in the site.
- Visit the Bookmark: you can access that folder quickly by click on the star icon and select the folder from the popup menu.
- Visit the browsing history: Click on the drop-down arrow icon and you will see the whole browsing history folders in the popup menu.
Fig. 3. Add Favorite Bookamrks
Conclusion
CrossFTP Pro makes it easy to manage multiple sites simultaneously.
This feature is available for CrossFTP Pro 1.86.6 or later.
--
CrossFTP is a FTP, SFTP, FXP, WebDav, Amazon S3, Amazon Glacier and Google Cloud Storage client for Windows, Mac, and Linux.
CrossFTP Team
http://www.crossftp.com/
CrossFTP Team
http://www.crossftp.com/
Sunday, October 28, 2012
Set Default Metadata/HTTP Header for Amazon S3 with CrossFTP
Metadata is widely used in S3 and other cloud storage systems for its storage object's description and HTTP Header's setting.
There are cases that you want to setup the default metadata for all your uploaded objects, e.g, define a common HTTP Header or expire date. To do this, you can choose Site Manager -> S3 -> Enable Default Metadata to allow the setting of the default metadata, and setup the metadata by press the "..." button.
You can setup the default metadata in the popup dialog. After press the OK button, the metadata will be saved for future transfers.
When a file is to be transferred to the remote site, CrossFTP will firstly calculate the general metadata for the file, including the file's original modification date, the compression algorithm, the encryption algorithm, mime type, etc. After that, the default metadata will be inserted into the object's metadata table before the transfer. The file transfers together with its metadata info to avoid additional operation cost.
You can check whether the file's metadata has been correctly setup by right click on the file, chose properties, and see the metadata tab.
There are cases that you want to setup the default metadata for all your uploaded objects, e.g, define a common HTTP Header or expire date. To do this, you can choose Site Manager -> S3 -> Enable Default Metadata to allow the setting of the default metadata, and setup the metadata by press the "..." button.
Fig. 1. Default Metadata Setup
You can setup the default metadata in the popup dialog. After press the OK button, the metadata will be saved for future transfers.
When a file is to be transferred to the remote site, CrossFTP will firstly calculate the general metadata for the file, including the file's original modification date, the compression algorithm, the encryption algorithm, mime type, etc. After that, the default metadata will be inserted into the object's metadata table before the transfer. The file transfers together with its metadata info to avoid additional operation cost.
You can check whether the file's metadata has been correctly setup by right click on the file, chose properties, and see the metadata tab.
This feature is available for CrossFTP Pro 1.86.2 or later.
--
CrossFTP is a FTP, SFTP, FXP, WebDav, Amazon S3, Amazon Glacier and Google Cloud Storage client for Windows, Mac, and Linux.
CrossFTP Team
http://www.crossftp.com/
CrossFTP Team
http://www.crossftp.com/
How to Sign Private Distribution's URL with CrossFTP
To sign a URL for private distribution's object, you firstly need to setup a private distribution with read permission to your S3 objects. Check this blog for how to properly setup the private distribution.
To create the sign URLs, you can select the files you want to sign, and choose "URL..." from the popup menu. The URL will be shown to assist your URL Sign tasks. Our URL generator dialog can detect whether an S3 object is associated with private Download/Stream distribution, and then assist to create the corresponding HTTP/HTTPS/RTMP/HTML URLs, as shown in Fig. 1.
Before start to sign the URL, defining the secure signing policy's definition is a precondition:
The policies list dialog will be shown as Fig. 2. You can use "New" button to create the new policy, "Edit" button to edit an existing policy, "Delete" button to remove a policy, "Save as" and "Load from" button to export/import the policies.
Canned Policy: a "simplified" policy definition that uses default options for your signed URL's behaviors, as shown in Fig. 3. Key pair ID and Private Key file are the most importation items in this dialog.
For the download distribution, you should choose HTTP/HTTPS radio button, choose the prefixed distribution URL in CNAME drop-down box, select the proper signing policy, and then press "Generate" button to sign the distribution, as shown in Fig. 1.
For the stream distribution, you should choose RTMP/HTML radio button, choose the prefixed distribution URL in CNAME drop-down box, select the proper signing policy, and then press Generate button to sign the distribution, as shown in Fig. 5.
CrossFTP Team
http://www.crossftp.com/
To create the sign URLs, you can select the files you want to sign, and choose "URL..." from the popup menu. The URL will be shown to assist your URL Sign tasks. Our URL generator dialog can detect whether an S3 object is associated with private Download/Stream distribution, and then assist to create the corresponding HTTP/HTTPS/RTMP/HTML URLs, as shown in Fig. 1.
Fig. 1. URL Dialog
Before start to sign the URL, defining the secure signing policy's definition is a precondition:
Secure Signing Policy
You can setup the signing policies by choosing Tools -> Policies, or in the URL dialog and press the Signing policy: Configure button.The policies list dialog will be shown as Fig. 2. You can use "New" button to create the new policy, "Edit" button to edit an existing policy, "Delete" button to remove a policy, "Save as" and "Load from" button to export/import the policies.
Fig. 2. Policies Dialog
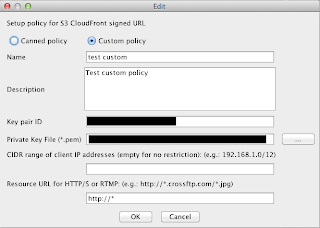
There are two types of signing policies: Canned Policy and Custom Policy. Here we introduce these policies one by one:Canned Policy: a "simplified" policy definition that uses default options for your signed URL's behaviors, as shown in Fig. 3. Key pair ID and Private Key file are the most importation items in this dialog.
Fig. 3. Canned Policy Modification
- Key pair ID is the ID number you will get from Amazon when you generate a Key Pair using Amazon web interface or when you upload your own key.
- Private Key File is the file you downloaded from Amazon web interface when you generate a Key Pair, or the private key file you used to generate the Key pair for uploading to Amazon.
Fig. 4. Custom Policy Dialog
- CIDR range: An optional range of client IP addresses that will be allowed to access the distribution, specified as a CIDR range.
- Resource URL: An optional HTTP/S or RTMP resource path that restricts which distribution and S3 objects will be accessible in a signed URL. For standard distributions the resource URL will be "http://distributionName/objectKey" (may also include URL parameters). For distributions with the HTTPS required protocol, the resource URL must start with "https://". RTMP resources do not take the form of a URL, and instead the resource path is nothing but the stream's name. The '*' and '?' characters can be used as a wildcards to allow multi-character or single-character matches respectively.
Generate signed URL for Private Distribution
URL dialog checks the S3 objects' associated distribution, and adds the private distribution's domain name/CNAMEs in the CNAME dropdown box. The URL dialog supports to generate HTTP/HTTPS/RTMP/HTML/FTP/Path type URLs.For the download distribution, you should choose HTTP/HTTPS radio button, choose the
For the stream distribution, you should choose RTMP/HTML radio button, choose the
Fig. 5. Sign URL for Stream Distribution
Conclusion
CrossFTP Pro makes it easy to manage your CloudFront distribution and URL signing.
This feature is available for CrossFTP Pro 1.86.2 or later.
--
CrossFTP is a FTP, SFTP, FXP, WebDav, Amazon S3, Amazon Glacier and Google Cloud Storage client for Windows, Mac, and Linux.CrossFTP Team
http://www.crossftp.com/
Saturday, October 27, 2012
How to Configure Private CloudFront Distribution with CrossFTP
Private CloudFront distribution is a good way to securely distribute the private download/streaming contents with Amazon CloudFront.
CrossFTP fully supports the private CloudFront distribution. To enable Private distribution, you can select a bucket, and right click to choose CloudFront -> Manage CloudFront Distributions..., and you can see a list of existing CloudFront distributions for the bucket, as shown in the Fig. 1.
To enable the private CloudFront distribution, you should choose the "Private Content" tab, and toggle the "Enable Private Distribution" button, as shown in Fig. 2.
To do this, two approaches are possible:
CrossFTP is a FTP and Amazon S3 client for Windows, Mac, and Linux.
CrossFTP fully supports the private CloudFront distribution. To enable Private distribution, you can select a bucket, and right click to choose CloudFront -> Manage CloudFront Distributions..., and you can see a list of existing CloudFront distributions for the bucket, as shown in the Fig. 1.
Fig. 1. CloudFront List Dialog
Create/Update the Private CloudFront Distribution
You can create a new CloudFront distribution by press the "New" button, or update an existing CloudFront distribution by press the "Edit" button. You can fill in the CloudFront distribution's basic information in the General Tab.To enable the private CloudFront distribution, you should choose the "Private Content" tab, and toggle the "Enable Private Distribution" button, as shown in Fig. 2.
Fig. 2. Enable Private Distribution
There may be a few concepts new for you in this dialog:
- Original Access Identity: this is a "virtual" user that is used for managing permissions that represents the private CloudFront distribution.
- S3 Canonical User ID: Associated with the Origin Access Identity, this is the user ID that you can use in ACL/permission setting dialog to grant permissions for the distribution. If you want to use distribution to share the contents, you need firstly to grant this ID the read permission in ACL/permission setting dialog.
- Trusted Signers: Only trusted signers are allowed to sign the distribution URL in S3. If you want to sign the private distribution URL for the download/streaming, you should at least add one trust signer, for example, by toggle "Add Myself as a Trusted Signer".
To find your account number, go to Your Account | Account Activity on AWS website, and look for the Account Number.
Grant the Permission for the Original Access Identity
You have to grant Read access to CloudFront Origin Access Identity account to make the files available for Private Distribution.To do this, two approaches are possible:
- Grant the read permission for the S3 Canonical User ID. Copy the S3 Canonical User ID as shown in Fig. 2., and add that user the read permission for the S3 object by right click on the object, and choose "ACL Setting...", as shown in the Fig. 3.
Fig. 3. Add S3 Canonical User ID with Read Permission
- Or you can configure the Bucket Policy to always grant Read access to Origin Access Identity, by right click on the Bucket, and choose "Bucket Policy..." to set up the policy.
CrossFTP is a FTP and Amazon S3 client for Windows, Mac, and Linux.
Tuesday, October 23, 2012
Setup Default Permission for File Transfer with CrossFTP
Permission is one of the most important security aspect for the files on the remote site. We pay high attention on this area, and to allow flexible permission control for file transfers, CrossFTP supports four types of permission setting policies for the upload and FXP tasks. You can find the permission setting options in the Site Manager -> Actions-> Default Permission.
As shown in the Figure 1, the available options are:
For S3 site, the permission will be assigned during the transfer, so that you don't need to pay for the permission change operation's fee.
This feature is available for CrossFTP 1.81.2 or later.
CrossFTP is a FTP and Amazon S3 client for Windows, Mac, and Linux.
Fig. 1. Default Permission Setup
As shown in the Figure 1, the available options are:
- No Inheritance: do not setup and arbitery permissions in the transfer process.
- From Parent: the file's permission will be copied from its parent folder's permission.
- From Source: the permission will be copied from the FXP transfer's source file.
- Default Permission: you can specify the default permission at the right side's "..." button. Transfered files will be assigned with this permission. For different FTP protocols, such as FTP (Fig. 2) and S3 (Fig. 3), different UI will be provided for setting the default permission. This is the recommended choice if you don't know which option to choose.
Fig. 2. Default Permission UI for FTP
Fig. 3. Default Permission UI for S3
For S3 site, the permission will be assigned during the transfer, so that you don't need to pay for the permission change operation's fee.
This feature is available for CrossFTP 1.81.2 or later.
CrossFTP is a FTP and Amazon S3 client for Windows, Mac, and Linux.
Monday, October 22, 2012
Client Side Encryption Support with CrossFTP
Security is one of the top consideration when choosing FTP/Cloud storage
client software and providers. CrossFTP puts security as top priority
in its design. For security of FTP/Cloud storage client software, it
includes 3 parts: 1, protect the FTP/Cloud storage sites' password in
local configuration; 2, protect the password and files during the data
transfer; 3, protect the files on the remote storage service provider.
In this document, we focus on point 3: how CrossFTP protect the files stored on the remote storage service provider: encrypt the files on local before sending them out.
Client side encryption for Amazon S3, Amazon Glacier, FTP, or WebDav are one important security feature CrossFTP Pro provides to enhance the data transfer security. To further enhance the transfer security, CrossFTP Pro supports client side encryption for for all FTP protocols it can handle, including FTP, SFTP, FTPS, WebDAV, Amazon S3, etc. After enable the client side encryption, in the upload process, all files will be firstly encrypted before they are transferred to the remote site. In the download process, the encrypted file will be decrypted after the file is downloaded from the remote site to the local drive. We will add ".aes" extension to the encrypted files to stand for the encryption.
We uses one of the strongest block ciphers available, 256-bit Advanced Encryption Standard (AES-256), for the encryption. 256-bit is the largest key size defined for AES.
To enable the client side encryption, you can choose Site Manager -> Security -> Enable Local Encryption, and input the password for the encryption, as shown in the figure. The password is encrypted stored in the site bookmarks file to ensure the security.
TIP: On a default JRE/JDK installation, AES is limited to 128-bit key size. Hence you will see AES-256 encryption failed with empty files. This is a remnant of import/export laws on cryptographic algorithm. To unlock larger AES key sizes, you need to download and apply the "JCE Unlimited Strength Jurisdiction Policy Files" (for latest JRE/JDK see at the bottom of this page).
Attention: You must make sure you enter the password correctly and remember the password. Otherwise, you cannot recover the encrypted files if you lost the configuration.
This feature is available for CrossFTP 1.86.2 or later.
CrossFTP is a FTP and Amazon S3 client for Windows, Mac, and Linux.
In this document, we focus on point 3: how CrossFTP protect the files stored on the remote storage service provider: encrypt the files on local before sending them out.
Client side encryption for Amazon S3, Amazon Glacier, FTP, or WebDav are one important security feature CrossFTP Pro provides to enhance the data transfer security. To further enhance the transfer security, CrossFTP Pro supports client side encryption for for all FTP protocols it can handle, including FTP, SFTP, FTPS, WebDAV, Amazon S3, etc. After enable the client side encryption, in the upload process, all files will be firstly encrypted before they are transferred to the remote site. In the download process, the encrypted file will be decrypted after the file is downloaded from the remote site to the local drive. We will add ".aes" extension to the encrypted files to stand for the encryption.
We uses one of the strongest block ciphers available, 256-bit Advanced Encryption Standard (AES-256), for the encryption. 256-bit is the largest key size defined for AES.
To enable the client side encryption, you can choose Site Manager -> Security -> Enable Local Encryption, and input the password for the encryption, as shown in the figure. The password is encrypted stored in the site bookmarks file to ensure the security.
TIP: On a default JRE/JDK installation, AES is limited to 128-bit key size. Hence you will see AES-256 encryption failed with empty files. This is a remnant of import/export laws on cryptographic algorithm. To unlock larger AES key sizes, you need to download and apply the "JCE Unlimited Strength Jurisdiction Policy Files" (for latest JRE/JDK see at the bottom of this page).
Attention: You must make sure you enter the password correctly and remember the password. Otherwise, you cannot recover the encrypted files if you lost the configuration.
This feature is available for CrossFTP 1.86.2 or later.
CrossFTP is a FTP and Amazon S3 client for Windows, Mac, and Linux.
Sunday, October 21, 2012
CrossFTP 1.86.2 Released
CrossFTP 1.86.2 is a major update. The main changes are:
* Adds sign URL support for S3 private distribution.
* Adds local encryption support for file transfer.
* Support enqueue the file delete operation for multi-thread processing.
* Adds Mac Mountain Lion and sandbox's support.
* Adds zebra line color to match Mountain Lion's finder style.
* Better compatbility for s3 compatible protocol, such as Ceph, etc.
* Solve FTP PASV/PORT firewall issue in Windows Vista/7/2008 with JDK 7 by fallback IPV4 network stack.
* Fix the private CloudFront update bug.
* Improved file context menu for easier understanding.
This update is recommended for all CrossFTP users.
CrossFTP Team
http://www.crossftp.com/
* Adds sign URL support for S3 private distribution.
* Adds local encryption support for file transfer.
* Support enqueue the file delete operation for multi-thread processing.
* Adds Mac Mountain Lion and sandbox's support.
* Adds zebra line color to match Mountain Lion's finder style.
* Better compatbility for s3 compatible protocol, such as Ceph, etc.
* Solve FTP PASV/PORT firewall issue in Windows Vista/7/2008 with JDK 7 by fallback IPV4 network stack.
* Fix the private CloudFront update bug.
* Improved file context menu for easier understanding.
This update is recommended for all CrossFTP users.
CrossFTP Team
http://www.crossftp.com/
Saturday, July 28, 2012
CrossFTP 1.81.4 Released
CrossFTP 1.81.4 is a bug fix update.
* Fix the multi-part upload's minimum part size issue.
* Fix the stream CloudFront distribution's delete issue.
* Fix the rtmp URL prefix error.
This update is recommended for all CrossFTP users.
CrossFTP Team
http://www.crossftp.com/
* Fix the multi-part upload's minimum part size issue.
* Fix the stream CloudFront distribution's delete issue.
* Fix the rtmp URL prefix error.
This update is recommended for all CrossFTP users.
CrossFTP Team
http://www.crossftp.com/
Friday, July 20, 2012
Amason S3 Multi-Part Upload with CrossFTP
CrossFTP supports the multi-part upload for Amazon S3. With Amazon S3's multi-part upload, you can achieve:
- You can upload larger file over 5G limit.
- You can make the upload more reliable, by separate the file into multiple parts, and retry only the failure part.
- You can fasten the upload speed by transfer the multiple parts simultaneously.
Note: If you meet some issue like the upload file is divided into too many parts, it is probably that the multi-part upload's part size is set too small. You need to set it up as a correct value.
Everything of multi-part upload happens automatically. The main upload file will be divided into multiple parts, and can transferred as separated part items simultaneously.

When all the child parts are uploaded, the main upload file will complete the multi-part upload.
This feature is available for CrossFTP 1.80 or later.
--
CrossFTP is a FTP, SFTP, FXP, WebDav, Amazon S3, Amazon Glacier and Google Cloud Storage client for Windows, Mac, and Linux.
CrossFTP Team
http://www.crossftp.com/
Saturday, June 02, 2012
CrossFTP 1.80c Released
CrossFTP is an excellent FTP client. CrossFTP Pro is a FTP client supporting SFTP, FXP, WebDav, and Amazon S3. CrossFTP 1.80c is a major update of CrossFTP. It significantly enhances the Amazon S3 upload, improves the WevDav compatiblity, and fixes a number of bugs. Here are the main change points:
* Support S3 multi-upload for large files' uploads.
* Set the default permission for upload.
* Set the default S3 metadata for S3 sites.
* Improve the WebDAV comparability by allowing to send "100-Continue" HTTP Header for server.
* Fix the URL creation bug for the CloudFront distributions.
* Fix the permission inheritance from parent's bug.
* Fix the permission inheritance from source's bug.
This update is recommended for all CrossFTP users.
CrossFTP Team
http://www.crossftp.com/
Subscribe to:
Comments (Atom)